Users tend to reuse passwords to make their life simple. This includes reusing the same passwords across multiple sites and using the same passwords for years and years.
This is bad of course. We see it in the news so frequently that no one is surprised that millions of accounts are compromised at companies every week. What happens to this compromised data? Very often it is dumped online where anyone can see it. In fact, a vast collection of compromised information from usernames and passwords to addresses to employment histories and more is or has been available online related to all of these compromised web accounts.
HaveIBeenPwned?
In short, this means that as of this writing, there is a collected library of half a billion actual passwords that have been used for logins to various web sites. All of these passwords are public and known to attackers. It is a common tactic to mine this database of known passwords to help gain access to other accounts (i.e., your accounts) by trying them all … or at least ones that seem like they could be related to you. This is very much more efficient than trying every possible password combination.
This consolidated password library has been collected and is maintained and updated by the web site HaveIBeenPwnd. This is a great site and it actually tracks a lot more than compromised passwords — you can use it to look up and discover if your email address, password, and other information has been compromised and in what data breaches, etc.
Better Password Management at LuxSci
LuxSci provides many configurable features that administrators can use to control the strength and life cycle of passwords employed by their users. These features are great for security and compliance and include:
- Customizable minimum character length up to 16 characters.
- Customizable need to include letters, numbers, and special symbols.
- Customizable checking for how “hard to guess” the password is using entropy calculations.
- Customizable automatic periodic password changes.
- Customizable blocking of password reuse (i.e., do tracking the hashes of the last 4 or 8 passwords used so that they can not be reused).
- Various options for two-factor authentication (Duo.com, Google Authenticator, SMS, and email).
- Customizable options to control how password resets work, if they are permitted at all.
Now, LuxSci has added one additional password management tool in the administrator’s arsenal:
- Automatic blocking of the use of any passwords that have been exposed in data breaches.
When administrators enable this feature, LuxSci uses the HaveIBeenPwned API to check and see if any proposed new password is in the database of previously breached passwords. If it is, the user is notified of that fact, of how many times it has been seen in breaches, and the user is forced to choose a different password.
Don’t worry, checking the HaveIBeenPwned API is very secure. Neither the actual password nor a hash of the password are sent to this third party so the API check is safe against even a man-in-the-middle from determining the proposed password (see their API docs if you are curious how they do that).
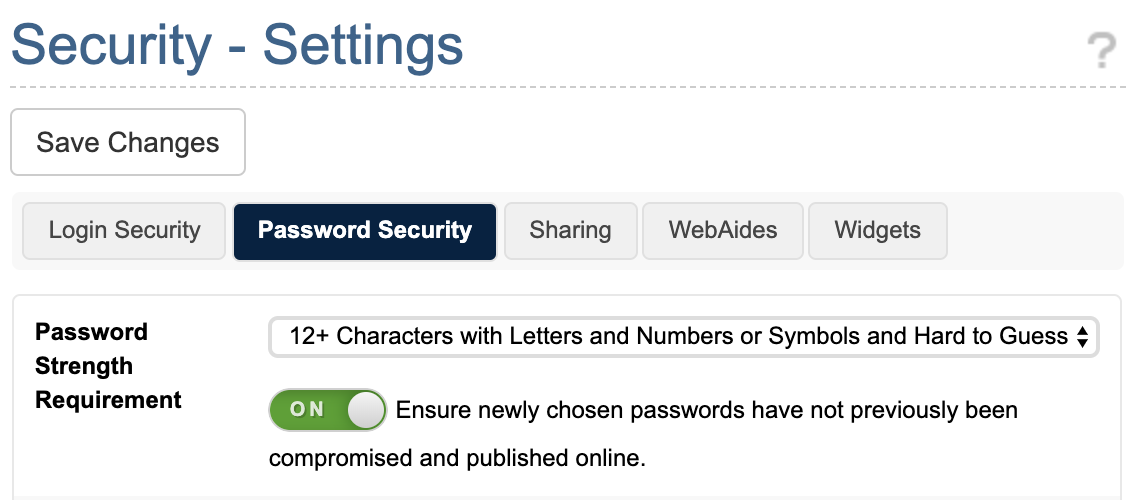
How to Enable Beached Password Blocking
This feature is enabled going foward for all new HIPAA-compliant customers and if you force “Maximal Security” settings in your account.
Otherwise, any customer can enable it explicitly by:
- Login to your LuxSci account as an account administrator.
- Go to Account Settings – Security – Settings.
- Click on “Password Security”
- Check the toggle next to: “Ensure newly chosen passwords have not previously been compromised and published online.”
- Press “Save Changes”