Email is an essential channel for most marketers. However, HIPAA regulations raise many questions for healthcare marketers who need to execute email marketing campaigns without violating patient privacy.
HIPAA is a complicated law that offers a lot of guidance but does not require the use of any specific technologies to protect patient privacy. The ambiguity causes a lot of confusion for marketers trying to integrate email into their marketing strategy. This article addresses some frequently asked questions about HIPAA-compliant email marketing and offers advice for securing patient data and futureproofing your marketing.
Do generic practice newsletters need to be protected?
Some marketers assume practice newsletters do not contain health information and, therefore, do not fall under HIPAA requirements. However, this assumption is often incorrect. Many are surprised to learn that protected health information can be implied from seemingly benign information.
In this way, many generic email newsletters often indirectly contain PHI because they are sent to lists of current patients. Email addresses are individually identifiable and combined with the email content; it may imply that they are patients of the practice. For example, say you send a “generic” newsletter to the patients of a dialysis clinic. An eavesdropper may be able to infer that the recipients receive dialysis. Therefore, the email reveals information about an individual’s health treatment, is PHI, and should be secured in compliance with HIPAA regulations.
In some cases, it can be complicated to determine what is PHI and what is not. Using a HIPAA-compliant marketing solution is best to avoid ambiguity and ensure security.
How Do I Find a HIPAA Compliant Email Marketing Vendor?
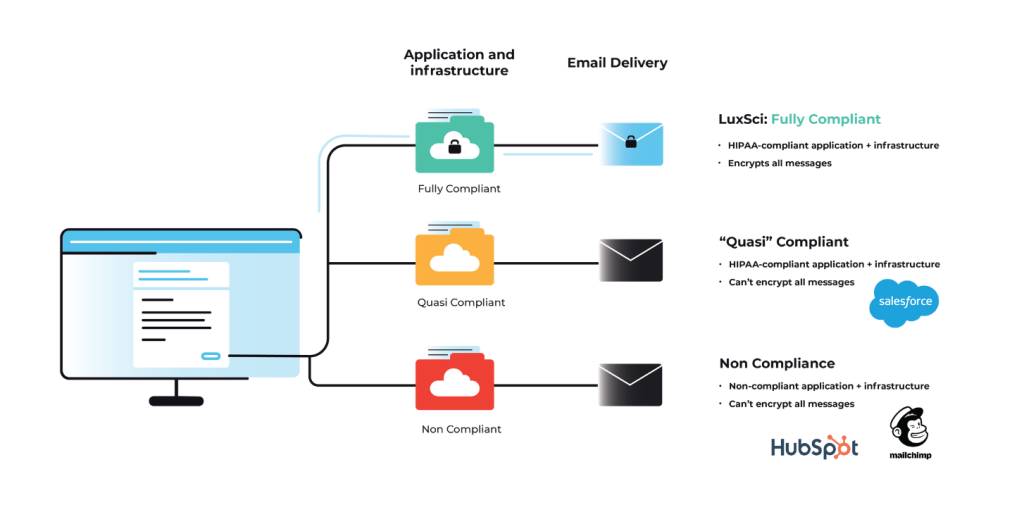
Unfortunately, using broadly popular email marketing platforms is not recommended. Many of these platforms were designed for e-commerce businesses and are not secure enough to meet HIPAA requirements. We do not recommend using a solution not specifically equipped to meet the healthcare industry’s unique security and compliance needs. To determine if your email marketing provider is compliant, they must meet three broad criteria at a minimum.
- The vendor must sign a Business Associate Agreement outlining how they plan to secure your data and what they will do in the event of a breach.
- Encrypt data at rest when it is stored in their systems.
- Encrypt email messages and data in transit as it is sent to the recipients.
Not all vendors will be up to the task. Carefully vet your email marketing vendors to ensure they are taking steps to secure data and protect patient privacy.
What is an Email API?
API is an acronym that stands for “Application Programming Interface.” An email API gives applications (like CRMs, CDPs, or EHRs) the ability to send emails using data from the application. Email APIs also return campaign data to the platform or dashboards so you can assess the effectiveness of your marketing efforts. Trigger-based transactional or marketing emails are ideal for sending with an email API. In this situation, emails are sent when pre-determined conditions in the application are met. Healthcare organizations may use email APIs to send appointment reminders using electronic health records system data about a patient’s upcoming appointment.
Email APIs enable the automation of common email workflows. However, they are not interchangeable with email marketing platforms. Email APIs do not include the contact management systems standard in most email marketing platforms because all that data lives within the application they connect to. In addition, email API tools typically do not include drag-and-drop editor tools or other design features that help your emails stand out.
Does HIPAA permit providers to send unencrypted emails with PHI to patients?
Encryption is an addressable standard under the HIPAA Security Rule, but that does not mean it is optional. The HIPAA Privacy Rule does not explicitly forbid unencrypted email. Still, it does state that “other safeguards should be applied to protect privacy reasonably, such as limiting the amount or type of information disclosed through the unencrypted email.”
In addition, the Department of Health and Human Services also states that “covered entities are permitted to send individuals unencrypted emails if they have advised the individual of the risk, and the individual still prefers the unencrypted email.” Some organizations use waivers to inform patients of the risks and acquire permission to send unencrypted emails.
However, we do not recommend this approach for several reasons:
- Keeping track of waivers over time and recording status changes and updates is challenging.
- Signed waivers do not insulate you from the consequences of a HIPAA breach.
- And finally, using waivers to send unencrypted emails doesn’t eliminate your other HIPAA obligations like data retention and disposal. Using a HIPAA-compliant solution is more manageable and eliminates ambiguity.
Can patients exercise their right of access by receiving PHI via unencrypted email?
Yes, but they must be fully informed of the risks and sign waivers acknowledging them. The caveats in the previous answer apply. It’s always better to utilize an encryption tool to protect patient data.
Is Microsoft 365 or Exchange 365 encryption sufficient for marketing emails?
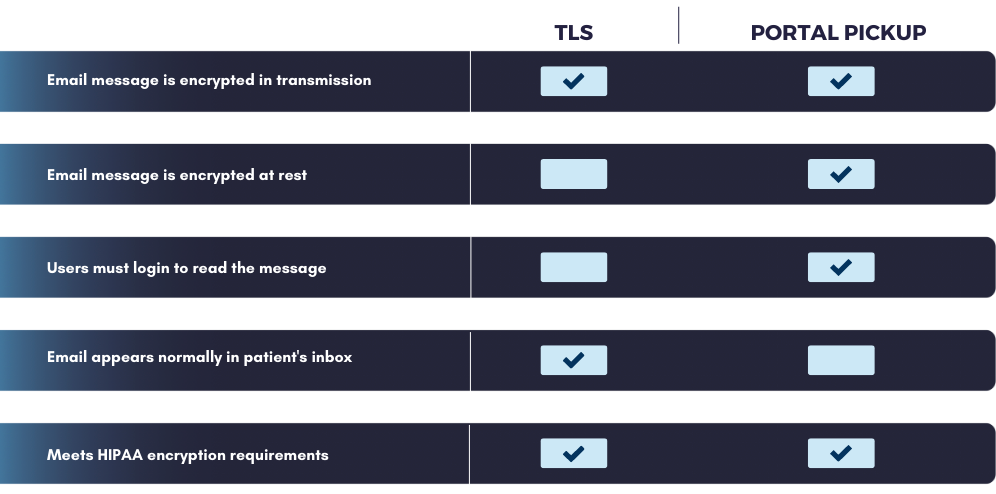
Microsoft 365 can be configured with Office Message Encryption (OME) to comply with HIPAA. However, the program is not well-suited to HIPAA email marketing. OME primarily relies on portal pickup encryption, in which the message is stored securely on a server and requires the recipient to log in to the portal to read the email. If you are a marketer trying to increase engagement, the portal adds a barrier to access that many will not cross. Light-PHI marketing messages are best sent using TLS encryption. TLS-encrypted messages arrive in the recipient’s inbox just like a regular email and do not require a user to log in to read the message.
In addition, Microsoft 365 is not configured to send high volumes of email. If you plan to send large marketing campaigns, you could unintentionally disrupt regular business communications by sending all the messages through the same infrastructure. You should separate your business and marketing email sending to protect your IP reputation and achieve your desired sending throughput.
What are common email marketing use cases for healthcare?
Email marketing in healthcare is not restricted to boring practice newsletters. When you utilize tools that enable the use of PHI in your targeting and personalization efforts, the sky is the limit. With consumer preferences shifting toward digital communications, marketers willing to utilize the email channel and tactics like segmentation and personalization can see better results.
Email is an excellent way to communicate with patients. A sampling of ways that healthcare marketers can use email include:
- engaging patients in their healthcare journey
- educating patients about their healthcare conditions and treatments
- improving attendance and scheduling
- retaining patients
- increasing preventative procedures
- collecting data on the patient experience
- improving patient satisfaction
Conclusion
HIPAA can be difficult to understand, but choosing the right tools and adequately vetting your vendors makes it easy to execute HIPAA-compliant email marketing campaigns. If you are interested in learning more about LuxSci’s easy-to-use, Secure Marketing platform, please contact our sales team.