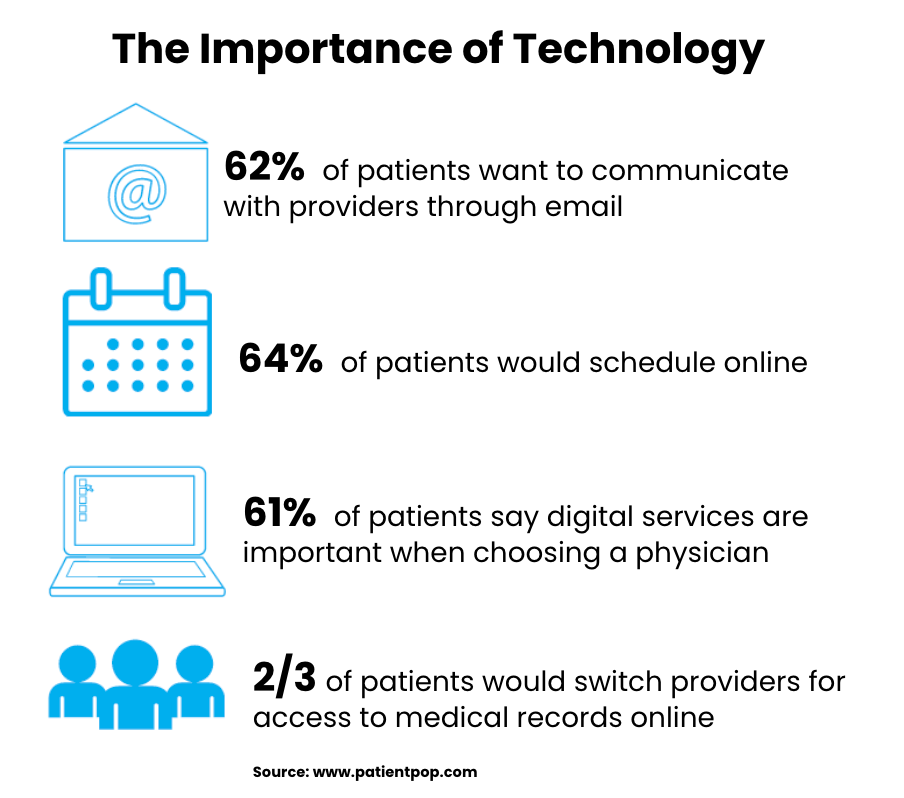
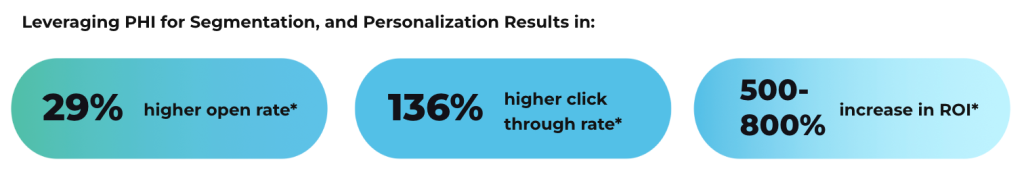
There are many crucial factors to consider when developing and executing successful healthcare communication campaigns. First and foremost, you must ensure the protected health information (PHI) under your organization’s care is handled securely, as mandated by Health Insurance Portability and Accountability Act (HIPAA) regulations, which begins with selecting the right HIPAA compliant email provider for your company’s needs.
With the right email services provider (ESP) in place, healthcare providers, payers, and suppliers can confidently use PHI in their patient and customer engagement campaigns – safe in the knowledge they’re aligned with HIPAA’s tight regulatory guidelines.
To help you choose the best HIPAA compliant email provider for your healthcare organization’s email outreach objectives, this post compares two of the most well-known HIPAA compliant services on the market: LuxSci and Zix Webroot (from here, simply referred to as Zix).
Comparing each email provider’s performance on several criteria, we’ll help you decide which solution best fits the needs of your healthcare organization and will help you better engage with your patients and customers.
LuxSci vs. Zix: Evaluation Criteria
In our evaluation of LuxSci vs. Zix, we’ll be using the following criteria:
- Data Security and Compliance: undoubtedly the most important factor when it comes to ensuring HIPAA-compliant email communication within healthcare organizations, this reflects the extent to which each platform secures sensitive patient data as per HIPAA’s regulations.
- Performance and Scalability: the email platform’s ability to facilitate high-volume email communication campaigns, which also, subsequently, encompasses the platform’s throughput and how well they’re able to scale in line with an organization’s needs.
- Infrastructure: if the email service provider has the necessary security infrastructure in place to both adequately safeguard PHI and support bulk email marketing campaigns.
- Marketing Capabilities: if the platform provides features that allow you to personalize and refine your patient engagement strategies.
- Ease of Use: how easy each email service is to use; a deceptively important factor in light of the urgent need for employee cyber threat awareness training.
- Other HIPAA-Compliant Products: if the platform offers complementary features that aid healthcare organizations with their broader patient engagement, and growth, objectives.
Now that we’ve covered the criteria by which we’ll be assessing each email platform, let’s compare LuxSci vs Zix to determine which is the best fit for your company’s needs.
LuxSci vs. Zix: How Do They Compare?
Data Security and Compliance
LuxSci prides itself on being a fully HIPAA-compliant email service provider, offering end-to-end, flexible, and automated encryption, giving it an advantage in the protection of patient data in the event of its exfiltration by cyber criminals. Additionally, LuxSci is HITRUST-certified, illustrating its additional commitment to data privacy legislation and the securing of PHI.
Zix is also fully HIPAA-compliant and, consequently, enables the use of PHI to personalize your email communications. That said, Zix doesn’t offer as many encryption options as LuxSci. Most notably, Zix doesn’t enforce Transport Layer Security (TLS) encryption or enable automated encryption. The absence of these features means that a healthcare organization’s security teams must perform more manual oversight when it comes to encryption of PHI, increasing the chance of human error.
Performance and Scalability
While Zix supports large email campaigns and provides detailed reporting functionality, LuxSci is the more prudent choice for high-volume email marketing campaigns.
LuxSci maintains the necessary infrastructure to ensure the reliable delivery of hundreds of thousands to millions of emails per month (i.e., throughput – 1000s of emails per hour), all while adhering to HIPAA’s strict guidelines on preserving patient privacy.
Infrastructure
In the same way that LuxSci have advantages over Zix on data security capabilities, it performs well in this category too, which makes sense, as the two factors are interwoven.
While offering a range of customary multi-tenancy infrastructure setups, Zix doesn’t accommodate dedicated, or single-tenancy, infrastructure options – for companies who can’t afford to depend on the security postures of the companies with whom they share servers. Zix, in line with its ability to facilitate large patient or customer engagement campaigns, provides enterprise-scale scalability.
Zix also provides high availability and robust disaster recovery capabilities, so healthcare organizations can retain their operational capabilities in the event of a cyber attack. Or, alternatively, an unforeseen physical disaster that compromises a company’s infrastructure (power outages, fires, storms, intentional damage, etc.).
That said, LuxSci possesses all these features in addition to more comprehensive single-tenancy options, scalability, and secure email hosting.
Marketing Capabilities
As with our comparisons of LuxSci against email platforms like Paubox and Virtru, it’s somewhat futile to compare each platform’s marketing capabilities – as neither LuxSci or Zix are marketing platforms, in the vein of Adobe Campaign or Oracle Eloqua, for example.
That said. LuxSci provides a HIPAA compliant marketing solution, offering automation, for streamlining email marketing campaigns, and, personalization options, for more engaging email communication campaigns.
Ease of Use
Both LuxSci and Zix perform admirably in this category, but the edge goes to Zix, as LuxSci implementations often involve the complexities that come with large-scale, high volume use cases.
LuxSci, however, is known for offering best-in-class customer support backed by HIPAA security experts, honed as a result of over 25 years of facilitating and supporting email communication strategies for healthcare organizations of all sizes.
Other HIPAA-compliant Products
With secure texting functionality, secure forms for HIPAA compliant data collection, and secure file sharing, LuxSci ranks well in this category. Zix, in contrast, provides only secure file sharing – though, because of Zix Webroot’s capabilities, offers superior secure file sharing to LuxSci.
Get Your Copy of LuxSci’s Vendor Comparison Guide
To discover how LuxSci and Zix stack up against the other leading email providers on the market when it comes to HIPAA compliance, take a look at our Vendor Comparison Guide. Evaluating 12 email delivery platforms, the guide offers comprehensive insights on what to consider when selecting a HIPAA compliant provider, and how to choose the best solution for you.