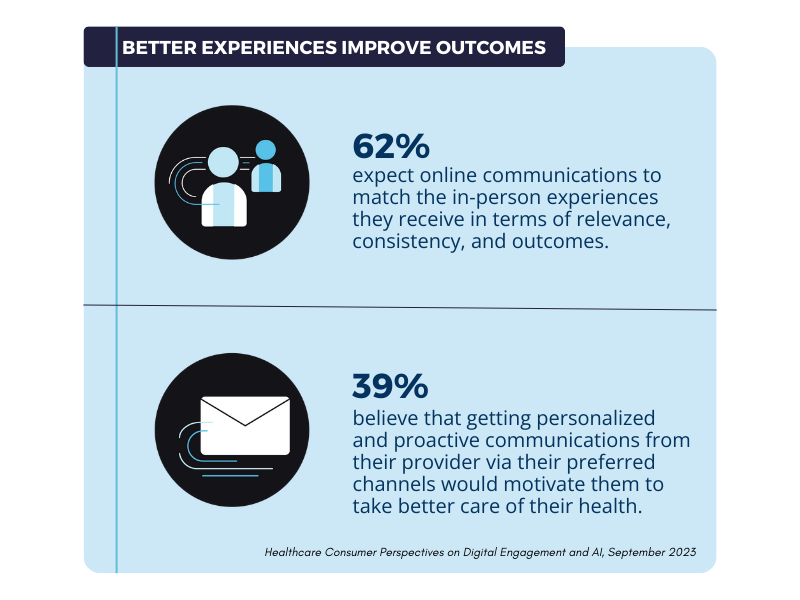
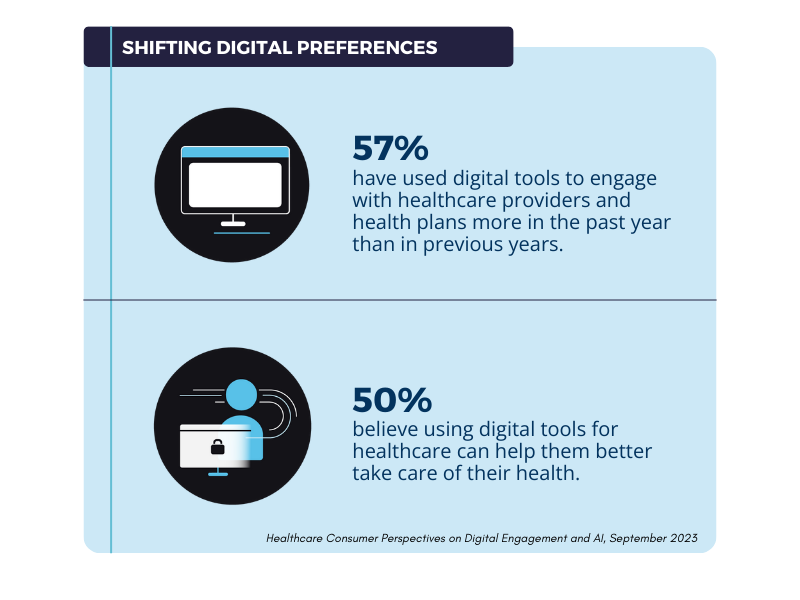
Patient expectations of healthcare providers have dramatically changed in the last decade. The introduction of technology and the widespread adoption of digital communications in other industries have increased the pressure on healthcare providers to provide a comparable experience.
The 2023 Healthcare Consumer Perspectives on Digital Engagement and AI report conducted by Dynata Research found that more patients are adopting digital tools to manage their health and want their providers to provide a consistent experience across all channels. To improve the patient experience, a personalized patient engagement strategy is necessary.
Personalized Patient Engagement Improves the Patient Experience
Healthcare organizations manage so much data that can be used to improve the patient experience. As audience segmentation and personalization techniques have become more common in other industries like e-commerce and personal care, consumers are starting to expect the same experiences from their healthcare providers.
For example, media streaming services make personalized recommendations for new shows based on what you have previously watched. People like these features because it helps them discover new content they may not know about. Likewise, patients are beginning to expect a similar personalized patient engagement experience from their healthcare provider. Suppose a patient wants to control their diabetes diagnosis and communicates with their provider about this at an appointment. Afterward, when they log into the patient portal or receive follow-up information, they expect to receive relevant information that aligns with that provider’s conversation.
Proactive, personalized patient engagement can also drive patients to make the right choices in managing their health. By sending patients the correct information at the right time in the context of their individual health journey, it is easier for them to manage their own health.
Shifting Preferences for Digital Tools Enable Personalized Patient Engagement
As more people are open to incorporating digital tools into their healthcare journeys, it has revealed new patient engagement opportunities. Several reasons led healthcare organizations to embrace digital tools. The coronavirus pandemic kicked off a necessary wave of digital transformation because of the rapid transmission of the disease through close contact. The desire to use these tools has remained strong even after institutions largely reopened in 2021. Patients have also shown no desire to go back to the way things used to be. Digital channels and tools like patient portals, email, medical devices, and mobile applications all make it easier for patients to manage their health on the go.
As patient preferences have shifted to embrace digital channels and technologies, organizations that can implement digital-first personalized patient engagement strategies intelligently are more likely to have satisfied and healthier patients. However, healthcare organizations must strive to provide a consistent experience across both in-person and digital avenues. According to the survey, the number one reason consumers would consider changing their healthcare provider is “complex or confusing experiences.” Poorly implemented and executed patient engagement can negatively impact the patient experience and retention, so it’s essential to be thoughtful in your approach.
How to Personalize the Patient Experience
Traditionally, HIPAA compliance requirements have made it difficult for healthcare providers to utilize protected health information (PHI) in personalized patient engagement efforts. Using PHI in communications is vital to craft messaging relevant to the patient’s health journey. However, when transmitting and storing PHI, HIPAA regulations must be followed to protect patient privacy.
The first step to executing personalized patient engagement involves selecting the right tools. Many traditional digital engagement tools are not designed to meet these stringent encryption and security requirements. By selecting tools that meet HIPAA’s technical requirements (like LuxSci’s Secure Marketing and Secure High Volume Email) and properly training employees, healthcare teams can employ the same segmentation and personalization techniques to reach patients with relevant and consistent communications.
Conclusion
Personalizing patient engagement is one way to improve patient marketing and retention. Contact us today to learn more about improving the patient experience with secure email communications.