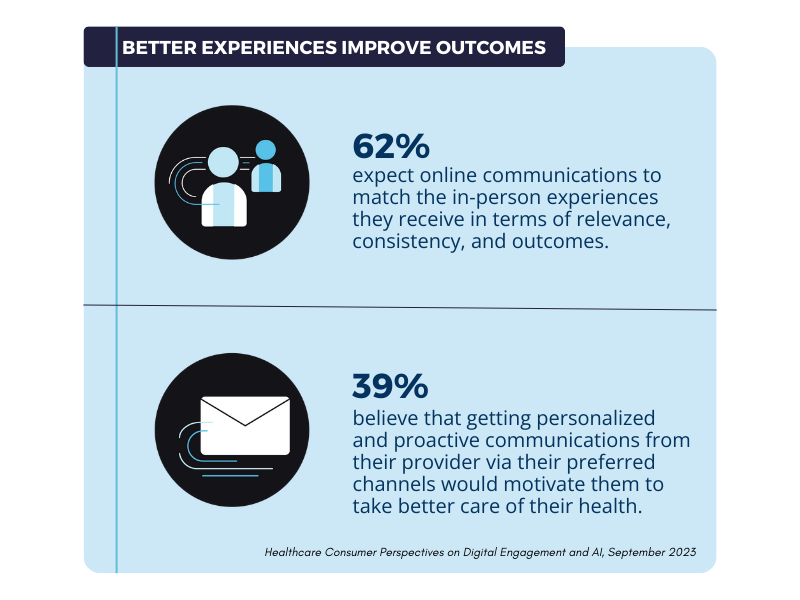
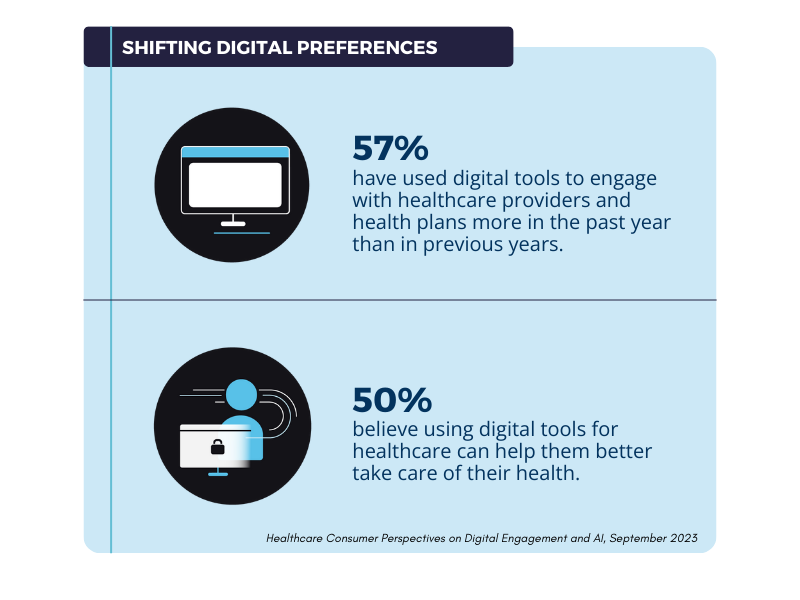
Email deliverability refers to the ability of emails to reach recipients’ inboxes successfully without being filtered into spam folders or blocked entirely by email service providers. This metric involves the entire journey an email takes from sender to recipient, including authentication protocols, sender reputation, content quality, and recipient engagement patterns. For healthcare organizations managing patient communications, provider networks, and supplier relationships, understanding email deliverability is highly important given the sensitive nature of healthcare data and the need for reliable communication channels.
How Email Service Providers Filter Messages
Email service providers use sophisticated algorithms to evaluate incoming messages and determine their appropriate destination. These systems analyze multiple factors simultaneously, including sender authentication records, message content, sending patterns, and recipient behavior. The filtering process occurs in real-time, with providers like Gmail, Outlook, and Yahoo applying machine learning models trained on billions of email interactions to identify potential spam or malicious content. Authentication plays a large role in this filtering process. Providers verify sender identity through SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) records. Healthcare organizations without properly configured authentication often find their appointment reminders, lab results, or billing communications relegated to spam folders, disrupting patient care workflows and administrative processes.
Sender Reputation and Its Impact on Healthcare Communications
Sender reputation functions as a digital credit score for email domains and IP addresses, influencing whether healthcare organizations can reliably reach patients, providers, and business partners. Email service providers maintain reputation databases that track sending behavior, bounce rates, spam complaints, and recipient engagement over time. A single domain or IP address with poor reputation can affect email deliverability across an entire healthcare network. Healthcare entities take on reputation challenges due to the nature of their communications. Patient appointment reminders sent to outdated email addresses generate high bounce rates, while automated billing notifications may receive spam complaints from recipients who forgot they subscribed to such communications. These factors can gradually erode sender reputation, making it increasingly difficult to reach patients with time-sensitive medical information.
Protocols for Healthcare Email Deliverability Security
Modern email deliverability depends heavily on proper implementation of authentication protocols that verify sender identity and prevent email spoofing. SPF records specify which mail servers are authorized to send emails on behalf of a domain, while DKIM adds cryptographic signatures to verify message integrity. DMARC ties these protocols together by instructing receiving servers how to handle emails that fail authentication checks. Healthcare organizations must configure these protocols carefully to avoid authentication failures that could block legitimate patient communications. A misconfigured SPF record might prevent appointment confirmation emails from reaching patients, while improper DKIM setup could cause lab result notifications to be filtered as spam. These authentication failures can have serious implications for patient care, particularly when dealing with urgent medical communications or time-sensitive treatment instructions.
Content Quality and Compliance Considerations
Email content quality directly affects email deliverability, with providers using advanced algorithms to evaluate message structure, language patterns, and formatting for spam indicators. Healthcare organizations must balance informative content with deliverability requirements, ensuring that medical communications reach their intended recipients without triggering spam filters. This balance becomes particularly challenging when dealing with complex medical terminology, prescription information, or insurance-related content that may resemble spam to automated filtering systems. HIPAA compliance adds another element of complexity to healthcare email content, as organizations must protect patient information while maintaining effective communication channels. Emails containing protected health information require extra security measures and careful content formatting to avoid both compliance violations and deliverability issues. The challenge is in creating compliant, informative communications that also pass through increasingly sophisticated spam filters.
Email Deliverability Performance
Tracking email deliverability metrics provides healthcare organizations with the data needed to identify and address communication issues before they impact patient care or administrative operations. Key metrics include delivery rates, bounce rates, spam complaint rates, and inbox placement percentages across different email providers. These metrics help organizations understand how their communications perform across various platforms and identify potential problems with specific communication types or recipient segments.
Healthcare organizations should establish monitoring systems that track deliverability performance across different communication channels, including patient portal notifications, appointment reminders, billing communications, and provider-to-provider messages. This approach helps identify patterns that might indicate authentication issues, content problems, or reputation concerns that could affect the organization’s ability to communicate effectively with patients and business partners.