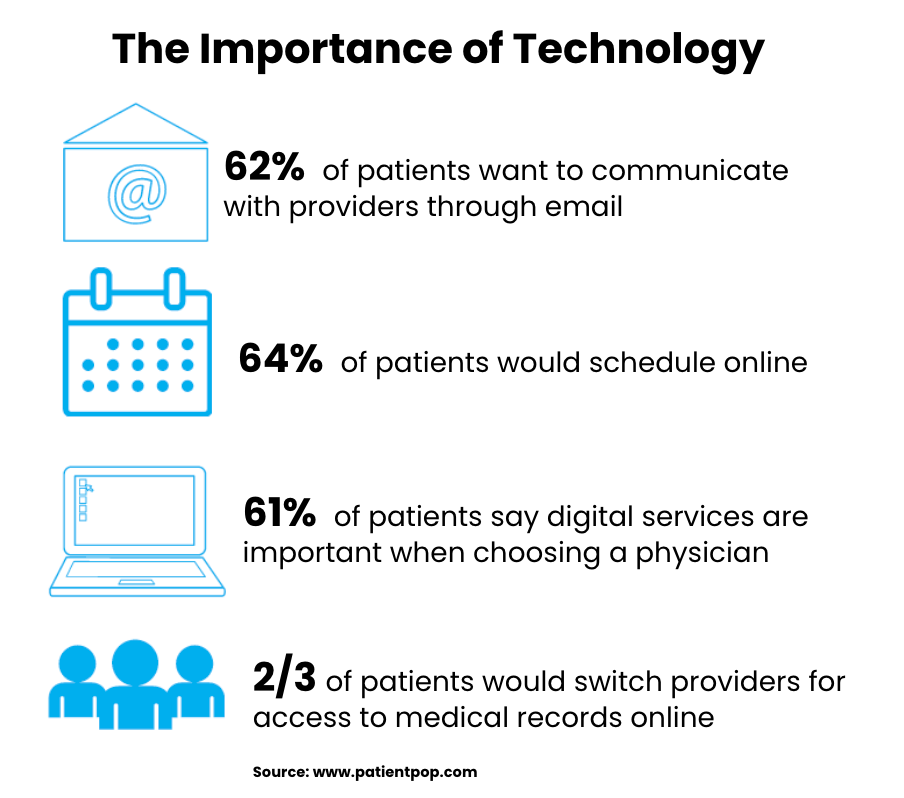
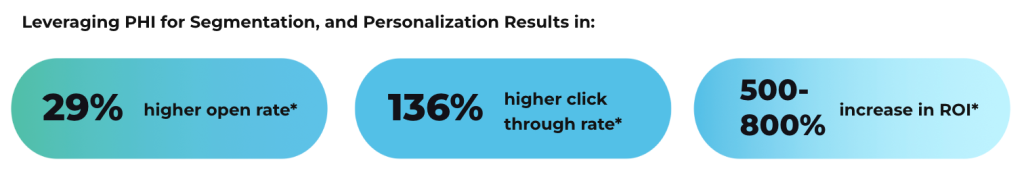
HIPAA email archiving is the systematic process of capturing, storing, and preserving electronic communications containing Protected Health Information in compliance with federal privacy and security regulations. Healthcare organizations use archiving systems to automatically collect email messages that contain patient data, maintain them in secure storage environments, and provide controlled access for authorized users.
The archiving process ensures that patient communications remain available for clinical care, regulatory compliance, and legal discovery while protecting the confidentiality and integrity of health information throughout extended retention periods. Medical practices and healthcare systems rely on email archiving to meet documentation requirements while managing the growing volume of electronic communications.
Why HIPAA Email Archiving is Required
Healthcare organizations require HIPAA email archiving to meet federal documentation standards and state medical record preservation laws. The HIPAA Privacy Rule establishes requirements for maintaining records related to patient information management, while state regulations often mandate specific retention periods for medical communications. Email messages containing treatment discussions, care coordination details, or patient scheduling, are all part of the medical record and must be preserved according to applicable legal timeframes.
Risk mitigation drives archiving implementation as healthcare organizations face increasing litigation and regulatory scrutiny. Medical malpractice cases frequently involve examination of communication records between providers, patients, and care teams. Organizations without proper archiving systems may face discovery sanctions or inability to defend against claims when relevant communications cannot be retrieved. Email archiving provides defensible documentation that supports clinical decision-making and protects against liability exposure.
Operational continuity benefits from archived communication access when healthcare providers need historical context for patient care decisions. Archived emails can reveal previous treatment discussions, specialist recommendations, or patient preferences that inform current care plans. Quick retrieval of communication history helps avoid duplicating previous conversations and ensures care teams have complete information when making treatment decisions.
Audit preparedness is achievable through systematic email archiving that preserves communication documentation for regulatory reviews. The Office for Civil Rights and other oversight agencies may request access to communication records during HIPAA compliance investigations. Organizations with properly implemented archiving systems can respond quickly to audit requests and demonstrate their commitment to patient information protection.
How Does HIPAA Email Archiving Differ From Standard Email Backup?
Security controls within HIPAA email archiving systems exceed those found in standard backup solutions. Archiving platforms implement encryption for data at rest and in transit, role-based access controls that limit user permissions, and audit logging that tracks all system interactions. Standard email backups may lack these specialized security features needed to protect patient information according to HIPAA Security Rule requirements.
Data organization in healthcare archiving systems focuses on patient-centric indexing and retrieval capabilities. The systems can organize archived communications by patient identifiers, treatment episodes, or healthcare provider relationships. Standard backup systems store emails chronologically or by user account without the specialized indexing needed for clinical or legal searches involving patient information.
To accommodate complex healthcare documentation requirements, HIPAA archiving platforms deliver robust HIPAA email retention features. The systems can apply different retention schedules based on message content, patient age, or state regulations while maintaining legal hold capabilities for litigation. Standard backup solutions lack the policy management tools needed to handle varied retention requirements across different types of healthcare communications.
Search functionality in healthcare archiving systems includes patient privacy protections and access controls that prevent unauthorized information disclosure. Users can search for communications related to specific patients or clinical topics while the system maintains audit trails of all search activities. Standard backup search tools do not include the privacy controls and audit capabilities required for handling patient information.
Components Supporting HIPAA Email Archiving Systems
Capture mechanisms within archiving systems automatically identify and collect email communications containing patient information as they flow through healthcare email infrastructure. Journal-based capture methods create copies of all email messages at the server level, ensuring complete collection without relying on user actions. Content analysis tools can identify messages containing ePHI through keyword detection, pattern recognition, and sender/recipient analysis to ensure appropriate archiving coverage.
Storage architecture for HIPAA email archiving incorporates multiple layers of data protection and redundancy. Primary storage systems maintain active archives with fast access capabilities for recent communications, while secondary storage tiers provide cost-effective long-term preservation for older messages. Geographic replication protects against data loss from natural disasters or facility damage while maintaining compliance with data residency requirements.
Access control systems manage user permissions and authentication requirements for archived email access. Role-based permissions ensure that healthcare workers can only access communications relevant to their job functions and patient care responsibilities. Multi-factor authentication adds security layers that protect against unauthorized access attempts while maintaining usability for legitimate users.
Audit and monitoring capabilities track all interactions with archived email communications to create compliance documentation. The systems log user access attempts, search queries, message exports, and administrative actions to provide complete audit trails. Automated reporting features help healthcare organizations monitor archiving system usage and identify potential security incidents or policy violations.
How to Select HIPAA Email Archiving Solutions
Compliance certification evaluation helps healthcare organizations identify archiving vendors that understand healthcare regulatory requirements. Vendors with HITRUST CSF certification, SOC 2 Type II reports, or similar security validations demonstrate their commitment to protecting healthcare information. Business Associate Agreement willingness and terms indicate vendor readiness to accept HIPAA compliance responsibilities for archived patient data.
Scalability assessment ensures that archiving solutions can accommodate current email volumes and future growth projections. Healthcare organizations examine storage capacity, user licensing models, and system performance under peak usage conditions. The evaluation includes reviewing vendor infrastructure capabilities and support for geographic expansion or practice acquisitions that may increase archiving requirements.
Integration requirements vary based on existing healthcare IT infrastructure and workflow needs. Archiving solutions need compatibility with current email platforms, electronic health record systems, and practice management applications. API availability and integration support affect how seamlessly archived communications can be accessed from within existing clinical workflows.
Total cost analysis encompasses software licensing, implementation services, ongoing maintenance, and storage expenses over the expected system lifespan. Healthcare organizations compare subscription models, per-user pricing, and storage-based fees while considering long-term retention requirements. The analysis includes potential cost savings from reduced legal discovery expenses and improved compliance management efficiency.
Implementation Challenges
Historical data migration requires careful planning to transfer existing email communications into new archiving systems while maintaining data integrity and compliance protections. Healthcare organizations need strategies for handling legacy email formats, preserving original timestamps and metadata, and ensuring complete transfer of patient communications. The migration process must maintain security controls throughout the transition period.
User training programs need development to help healthcare staff understand archiving system functionality and their responsibilities for communication compliance. Training covers proper email practices, archiving system search capabilities, and procedures for handling legal holds or audit requests. Change management support helps staff adapt to new workflows and archiving requirements without disrupting patient care operations.
Performance optimization is highly important as archiving systems handle increasing volumes of healthcare communications. Email traffic in large healthcare systems can be substantial, requiring archiving platforms that maintain capture rates and search responsiveness under heavy loads. Organizations need monitoring tools and vendor support to optimize system configurations for their specific usage patterns.
Policy development and enforcement require clear guidelines about archived communication access, retention schedules, and disposal procedures. Healthcare organizations need policies that address who can access archived communications, under what circumstances searches are permitted, and how to handle requests for patient communication records. Enforcement mechanisms ensure that archiving policies are followed consistently across the organization.
How to Maximize Email Archiving Investment
Workflow integration maximizes archiving value by making historical communications easily accessible within existing clinical applications. Healthcare organizations can implement single sign-on authentication and embed archiving search capabilities within electronic health record systems. Integration reduces the time healthcare workers spend switching between systems while maintaining security controls for patient information access.
Advanced search capabilities help healthcare organizations extract maximum value from archived communications through sophisticated query tools and analytics. Machine learning features can identify communication patterns, flag potential compliance issues, or surface relevant historical context for current patient care decisions. Analytics capabilities provide insights into communication volumes, response times, and collaboration patterns that support quality improvement initiatives.
Legal discovery preparation benefits from archiving systems that streamline the identification and production of relevant communications during litigation. Healthcare organizations can use search and filtering tools to quickly locate communications related to specific patients, time periods, or clinical events. Export capabilities and legal hold management reduce the time and cost associated with responding to discovery requests.
Compliance monitoring automation helps healthcare organizations maintain ongoing oversight of their email archiving practices and identify potential issues before they become violations. Automated reports can track archiving coverage, identify gaps in communication capture, and monitor user access patterns for unusual activity. Proactive monitoring supports continuous improvement in archiving practices and compliance management