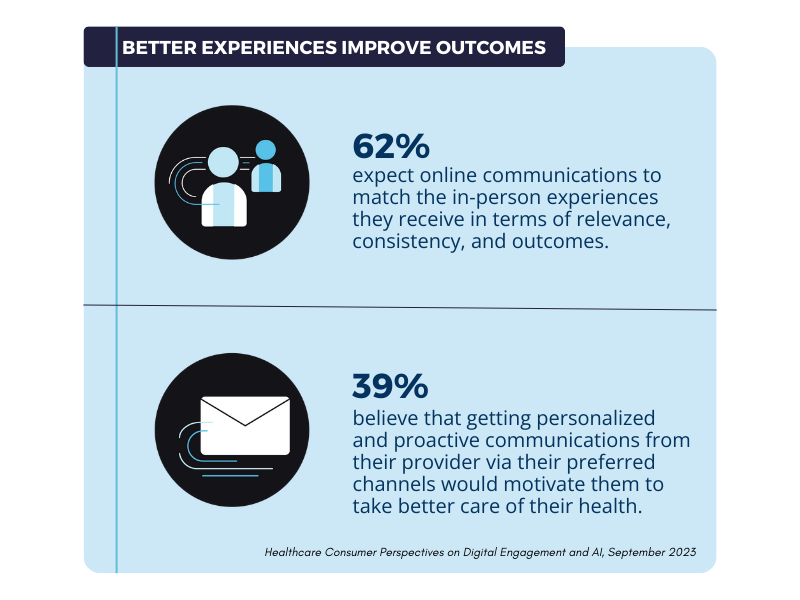
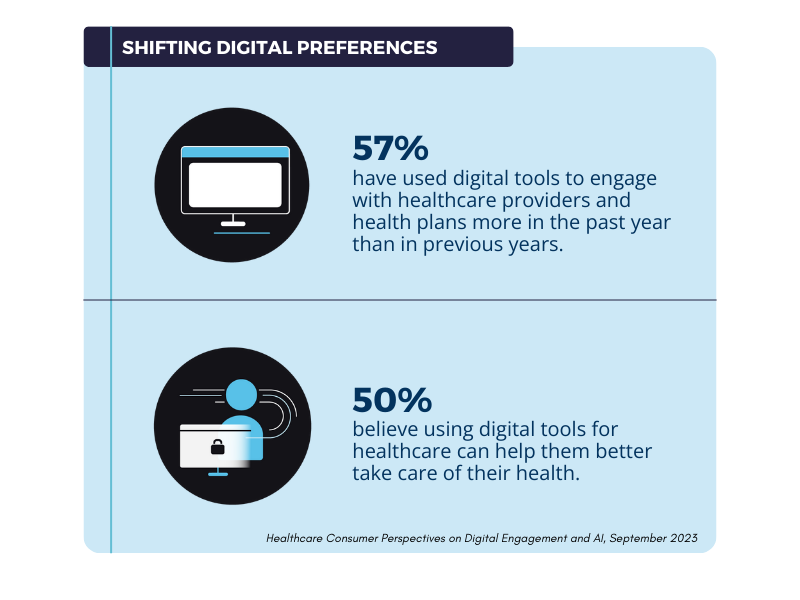
Yes, HIPAA compliant email is available through specialized platforms and services designed specifically for healthcare organizations that need to transmit protected health information securely. HIPAA compliant email solutions include encryption, access controls, audit logging, and other security features required to meet regulatory standards for protecting patient information during electronic communication. Healthcare providers, payers, and suppliers can choose from various HIPAA compliant email options that range from standalone secure messaging platforms to integrated solutions that work with existing healthcare systems. Understanding available HIPAA compliant email solutions helps organizations select appropriate tools for their communication needs while maintaining regulatory compliance and protecting patient privacy.
Types of HIPAA Compliant Email Solutions
Several categories of HIPAA compliant email solutions serve different organizational needs and technical requirements. Cloud-based secure email platforms provide hosted solutions that require minimal technical infrastructure while offering enterprise-grade security features. These platforms handle encryption, server maintenance, and security updates, allowing healthcare organizations to focus on patient care rather than email system management. On-premises HIPAA compliant email systems give organizations direct control over their email infrastructure and data storage locations. Hybrid solutions combine cloud convenience with on-premises control, allowing organizations to customize their email security approach based on specific requirements. Email encryption gateways work with existing email systems to add HIPAA compliance features without requiring complete system replacement.
Security Features in HIPAA Compliant Email Platforms
HIPAA compliant email platforms include end-to-end encryption that protects messages and attachments from unauthorized access during transmission and storage. Transport Layer Security protocols secure connections between email servers, while message-level encryption ensures that only intended recipients can read email content. Digital signatures verify sender authenticity and message integrity, preventing tampering or impersonation. Multi-factor authentication requires users to provide additional verification beyond passwords before accessing email accounts. Access controls limit which users can send emails to external recipients and which types of information can be included in different message categories. Automatic data loss prevention features scan outgoing emails for protected health information and apply appropriate security measures or block transmission of potentially sensitive content.
Business Associate Agreements and Vendor Requirements
Healthcare organizations using HIPAA compliant email services need business associate agreements with their email providers to ensure regulatory compliance. These agreements specify how email vendors will protect patient information, limit data use to authorized purposes, and report security incidents or unauthorized disclosures. Email providers operating as business associates must implement appropriate safeguards and allow healthcare organizations to audit their security practices. Vendor selection criteria should include security certifications, compliance track records, and technical capabilities that meet organizational requirements. Service level agreements define uptime expectations, support response times, and data recovery procedures. Due diligence processes help verify that email providers have appropriate security controls and compliance programs before entering into business relationships.
Implementation Challenges and Solutions
Healthcare organizations implementing HIPAA compliant email often encounter workflow disruptions as staff adapt to new security procedures and software interfaces. Training programs help users understand proper email security practices and organizational policies for handling protected health information. Change management strategies address resistance to new procedures and ensure that staff members understand the importance of email security compliance. Technical integration challenges arise when connecting HIPAA compliant email systems with existing healthcare applications and databases. Application programming interfaces enable custom integrations that streamline workflows while maintaining security standards. Migration planning addresses data transfer from legacy email systems and ensures that historical communications remain accessible when needed.
Cost Considerations for HIPAA Compliant Email
HIPAA compliant email solutions involve various cost components including software licensing, implementation services, ongoing support, and staff training expenses. Per-user subscription models allow organizations to scale email security based on their actual usage patterns. Enterprise licensing agreements may provide cost advantages for larger healthcare organizations with many email users. Hidden costs can include system integration expenses, data migration fees, and productivity losses during implementation periods. Return on investment calculations should consider potential savings from avoiding HIPAA violation penalties, reduced risk of data breaches, and improved operational efficiency from streamlined secure communication processes. Long-term cost analysis helps organizations budget appropriately for ongoing email security requirements.
Selecting the Right HIPAA Compliant Email Solution
Healthcare organizations should evaluate HIPAA compliant email options based on their specific communication patterns, technical infrastructure, and regulatory requirements. Feature comparisons help identify which platforms offer the security capabilities and integration options needed for particular use cases. Pilot testing allows organizations to evaluate user experience and system performance before making long-term commitments. Vendor demonstrations provide opportunities to assess ease of use, administrative features, and customer support quality. Reference checks with similar healthcare organizations offer insights into real-world performance and implementation experiences. Decision frameworks that consider security requirements, usability needs, and budget constraints help organizations select HIPAA compliant email solutions that will serve their long-term communication and compliance objectives effectively.