The Benefits of Using PHI in Patient Communications
Wednesday, March 15th, 2023Some healthcare organizations do not allow PHI to be sent outside the patient’s health record. However, by allowing your marketing and administrative teams to use PHI in patient communication, you can streamline operations, improve the patient experience, and increase revenue.
Although the healthcare industry is traditionally slow to adopt new technologies, the past few years have rapidly accelerated the shift to digital communications. The reasons for these shifts are varied and will be explored in detail below. No matter the reason, one thing is certain- organizations adapting to the modern digital age are thriving by using both HIPAA compliant email and HIPAA marketing, while those resisting change are falling behind in meeting patient expectations.
Changing Technology Preferences
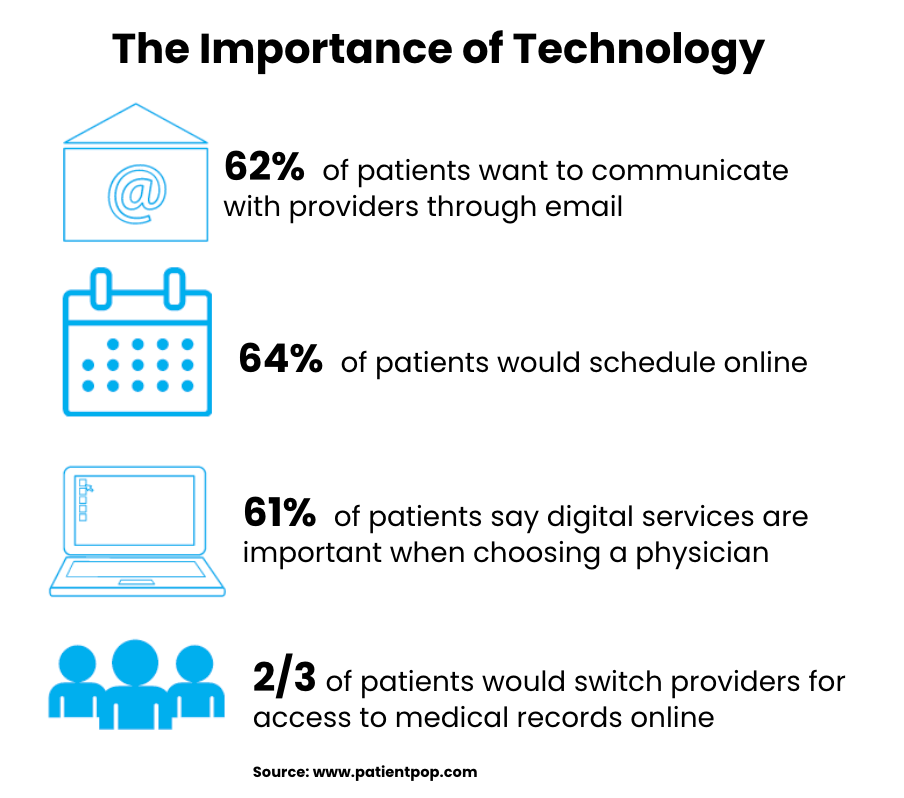
Rapid technological innovation has made it possible to communicate securely at scale. As broadband access has increased, people are incorporating it into their daily lives. In 2022, 92% of Americans reported using email, and 49% checked it every few hours. Many people now prefer to receive business communications via email because it is asynchronous and can be engaged with when it fits into their schedules.
Healthcare organizations that utilize email for external communication are experiencing better response rates and fewer patient no-shows. Email already fits into the daily lives of many patients and doesn’t require them to take extra steps to receive information about their healthcare journey.
The Rise of Healthcare Consumerism
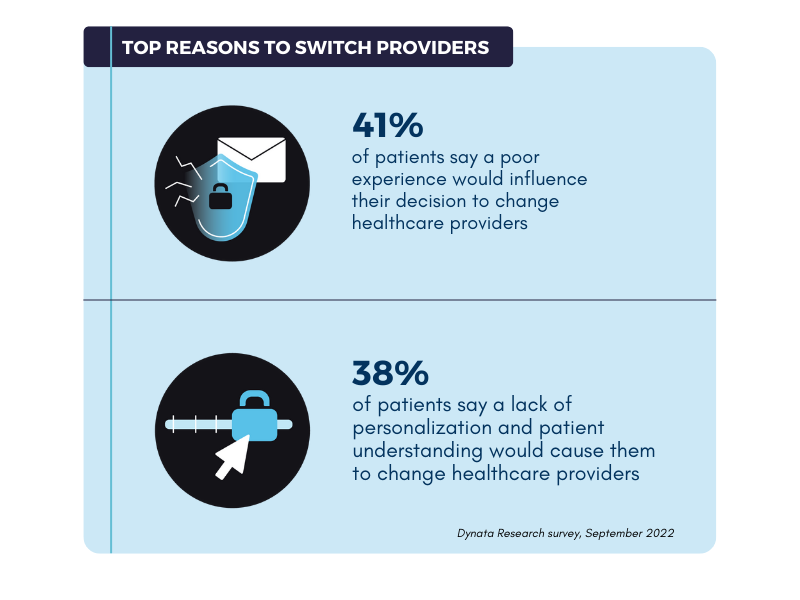
Healthcare consumerism refers to patients’ personal choices and responsibility in paying for and managing their health. Patients are no longer stuck with one provider or practice. They have more choices than ever and will shop around for new providers if unsatisfied with their experience.
If healthcare providers are not delivering a digital experience that meets patient expectations, they could risk losing patients and revenue.
In addition, as younger generations are taking control of their healthcare, they are used to digital-first experiences that are personalized to their needs. If organizations are unwilling to invest into personalized digital patient experiences, they will not adequately serve the next generation of healthcare consumers.
Staffing Challenges
The healthcare industry is not immune to recent staffing challenges. Staffing shortages have left fewer employees available to do more tasks, including patient care. Introducing digital technology into your patient communication strategy can help automate and streamline common communication workflows like:
- Appointment reminders
- Pre- and post-procedure instructions
- Health education messages
- Vaccine reminders
- Medication adherence reminders
- Billing
Automating common workflows frees up time for staff to focus on urgent patient needs and improves the patient experience.
How to Safely Use PHI in Patient Communications
Patients are already communicating with their healthcare providers one-on-one via email. The question is, how can you protect this data while communicating at scale for marketing and educational purposes? There are tools (like LuxSci’s Secure Marketing and Secure High Volume Email solutions) that are designed to support the unique security needs of the healthcare industry while providing the personalized digital experience that patients desire.
Protecting PHI in Patient Communications
PHI needs to be protected in emails with advanced encryption technology. TLS encryption should be used as often as possible because it provides a user experience like regular email without requiring a portal login. For marketing and patient education emails, TLS is sufficient to protect data and allows patients to readily engage with the email content. By properly vetting and choosing the right vendors, marketing and administrative teams can communicate with patients via email without violating HIPAA.
Personalization at Scale
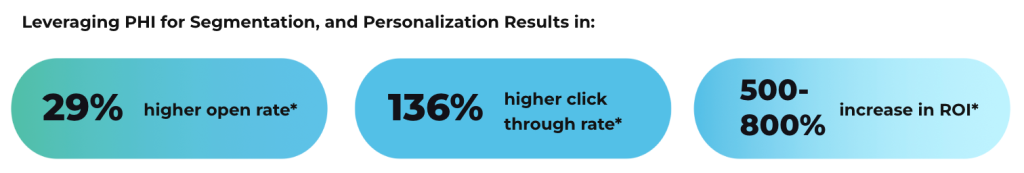
The power of PHI is undeniable. When healthcare marketers can harness healthcare data to create ultra-personalized campaigns, it increases their relevance and the likelihood that the content will be engaged with, delivering a better ROI. Our solutions integrate via API to securely personalize messages and trigger emails when specific conditions are met. This allows marketers to send relevant messages at the right time when it is relevant to the patient’s healthcare journey.
Modern technology is needed to serve today’s patients. Meeting patients where they are with the information they need on the channels they prefer is vital to improving healthcare outcomes for the most vulnerable populations. Using PHI in patient communications gives your organization a comparative advantage by providing a better patient experience.