Find The Right HIPAA Compliant Email Marketing Automation Platform
Saturday, June 15th, 2024If you are subject to HIPAA regulations think twice before sending off that marketing email blast to your customers. If your emails contain ePHI, stop and make sure you are using a HIPAA compliant email marketing automation platform before sending.
Not all email marketing platforms were designed with HIPAA marketing in mind. In fact, it can be difficult to figure out which vendors will allow you to send HIPAA compliant emails on their platforms. We created this list of five questions to help you screen potential HIPAA compliant email marketing automation platform vendors for compliance.
1. Is your email marketing automation platform HIPAA compliant and HITRUST certified?
It’s a simple question, but if the vendor does not mention anything about HIPAA or HITRUST certification on their website, it’s a good indicator that they are not secure enough to be compliant. As you probably know, HIPAA regulations can be onerous, and many companies do not have the time, expertise, or desire to update their technology. On the other hand, if they have taken the time and spent the money to invest in the serious security steps needed for HIPAA compliance, you should be able to find something about it in their marketing.
2. Will the vendor sign a Business Associate Agreement?
If you are sharing ePHI with a vendor (including lists of patient names and email addresses), you must have a BAA in place that outlines their responsibilities to protect your ePHI. If a vendor will not sign a BAA with you, it is an obvious sign that you cannot use their platform for HIPAA-compliant email marketing.
However, even if a vendor will sign a BAA, it does not mean that you can use their platform and comply with HIPAA. Read the fine print! Some companies have very restrictive BAAs that severely limit the functionality of the platform and prevent you from sending emails. We call these vendors “quasi” compliant. The only comply with HIPAA, if you abide by strict rules that prevent you from actually using their solution.
For an example, take Constant Contact. They will sign a BAA. However, they explicit state in their BAA that you:
“Should not use our systems for transmitting highly sensitive PHI (for example: mental health, substance abuse, or HIV information). Our application was not built for electronic medical records (EMR). If you have such information to send, please do not use Constant Contact.”
Constant Contact does not encrypt outbound emails, making it a poor choice for a HIPAA-compliant email marketing vendor. Depending on your email use cases, you could be unable to send any emails on their platform. Even worse, if you mistakenly send emails that contain ePHI you will be held liable for violating HIPAA, not Constant Contact, because you violated the terms of the BAA.
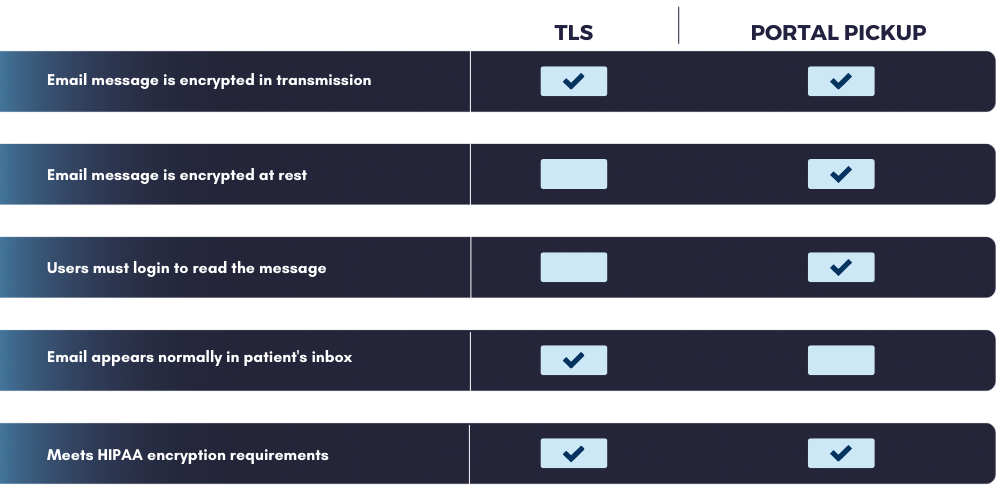
3. Does the email marketing platform protect data at rest and in transit?
Encryption is an addressable standard as part of the HIPAA Security Rule. Encryption is highly recommended to protect ePHI in all digital communications. Many email marketing platforms have adopted encryption methods that are secure enough to protect ePHI while it remains in their systems. However, that’s not enough to comply with HIPAA. You should specifically ask about their ability to encrypt outbound emails. Data in transit is extremely vulnerable to malicious actors, and therefore you need to encryption to protect emails containing ePHI. If a vendor does not provide encryption for outbound marketing emails then you should not consider using them.
4. How does the email marketing platform encrypt emails?
If a vendor says that they do encrypt outgoing messages, it’s important to consider these additional questions.
- How are they encrypting those emails?
- Do the encryption methods match your email use cases?
As a marketer, you want your emails to directly reach the recipient with as little friction as possible. If the recipient has to login to another platform to read the email, it’s unlikely to be read. A good HIPAA-compliant email marketing platform will use TLS encryption to send marketing messages directly to inboxes that support it. Emails sent with TLS encryption appear just like any other message directly in the recipient’s inbox.
However, there may be scenarios when you need to use more secure encryption methods. We recommend finding an email marketing vendor that is flexible and will let you select the right method of encryption for any type of message. For example, you may want to use a portal-based encryption method to send highly sensitive messages. Either way, make sure your vendor can support your needs with the right type of email encryption.
5. Does the platform allow you to send ePHI in the body of your emails?
Finally, the most important question to ask is: can I include highly sensitive patient information in an email? If you cannot, you can’t use the full power of the email marketing platform to create targeted, personalized and relevant messages. At best, you can only send generic office newsletters. If you want to create the types of marketing emails that will drive ROI and improve patient engagement, utilize your patient data for personalization and segmentation.
HIPAA Compliant Email Marketing Automation Platform
LuxSci’s Secure Marketing automation platform was built from the ground up with HIPAA marketing in mind. If you would like to learn more about how to create compliant email marketing campaigns utilizing ePHI, please let us know.