What is a Secure Email Gateway?
Tuesday, October 24th, 2023As threats to email security are increasing, organizations are looking for ways to enhance their security and reduce risk. One option is a secure email gateway. In this article, we review what secure email gateways are and how they can be used to secure sensitive data as it flows into and out of your accounts.
Protect Your Accounts With A Secure Email Gateway
Secure email gateways are an excellent way to strengthen the security of your email accounts without a costly switch to a new email provider. They layer on top of your existing email accounts to encrypt messages, scan for threats, and even capture messages for archival or backup purposes. They can also hide the sender’s IP address because messages are routed through another email infrastructure before delivery to the recipient. If you are concerned about increasing risks to sensitive data, secure email gateways offer a simple and effective way to enhance your email security.
How Do Secure Email Gateways Work?
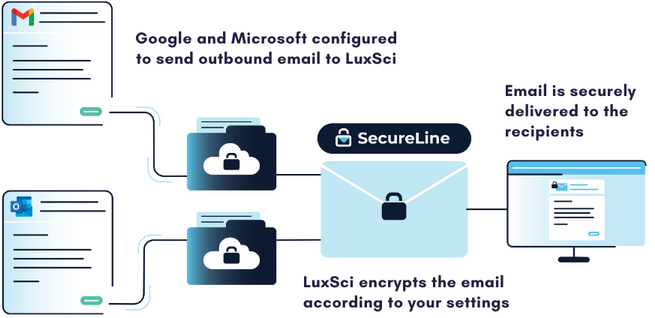
When using a secure email gateway, your messages are routed to a separate server before being sent or received. When sending an outbound message with LuxSci’s Secure Connector, it is routed through our SecureLine encryption before being securely delivered to the recipient. A copy of the message may also be sent to an independent email archive to help meet compliance requirements for message retention.
For incoming messages, the gateway can employ email filtering technology to quarantine suspicious messages. These technologies can scan incoming messages and prevent spammers and scammers from reaching employee inboxes and wreaking havoc. Just like with outbound email sending, the gateway can also capture a copy of inbound messages and retain them in an independent message archive.
The exact features of a secure email gateway will vary from vendor to vendor, but these represent some of the core functions that these tools provide. Simply put, a secure email gateway protects both incoming and outgoing messages to ensure that sensitive data is guarded from threats.
Why Choose a Secure Gateway?
There are two main reasons to implement a secure email gateway: the security and compliance benefits and their ease of use. Let’s look at each.
Compliance and Security Benefits
Many companies, like healthcare organizations, must comply with regulations for protecting patient or customer data. Many organizations grapple with the best way to secure potentially sensitive communications without interfering with or slowing down critical business workflows. Because secure email gateways layer on top of existing email accounts, they offer a speedy way to bring your organization into compliance with data security and retention guidelines.
As email continues to be an important channel for essential business communications, all organizations can benefit from protecting their employee accounts and reducing their risk and liability.
Easy to Administer and Use
Another benefit of using a secure email gateway is that your organization does not need to switch your primary email provider to enhance its security. Changing to a more secure email provider can be extremely challenging, especially if you have a lot of users with a lot of data that needs to be migrated to a new system. Add on the training time, and some organizations will find that switching email providers is a significant burden on the organization.
Installing a secure email gateway is very easy for account administrators and often does not require additional training or implementation for email users. Employees can continue to use their regular Microsoft or Google email accounts and do not need to take additional steps to learn an entirely new email program. With 73% of breaches in the healthcare industry caused by human factors, implementing tools that don’t rely on employee decision-making is essential.
Learn More About LuxSci’s Secure Connector
LuxSci’s Secure Connector is unlike other secure email gateways in that it encrypts every email automatically to reduce the risk of breaches caused by human errors. LuxSci provides the flexibility to opt-in to more secure methods of encryption for highly sensitive messages. Email filtering and archival tools are also available to reduce risk and improve resilience in the case of a cyber incident. Contact our sales team to learn more about our email security tools.